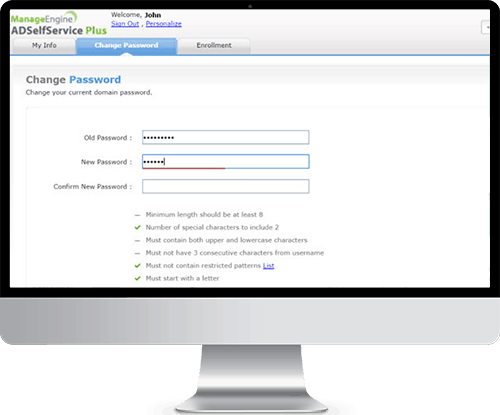
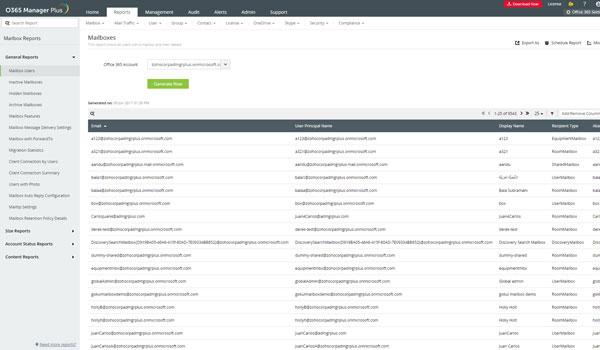
IT Compliance and Log Management
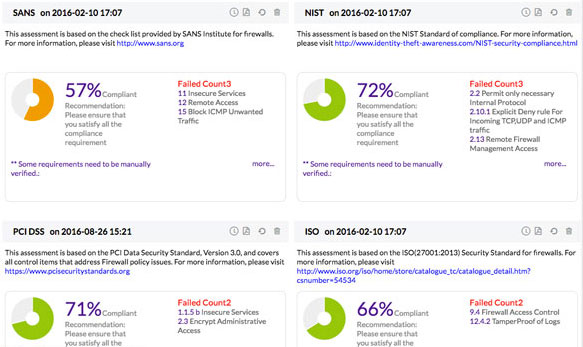
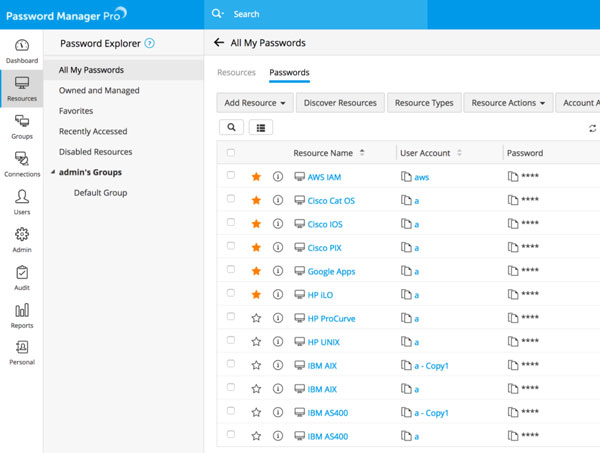
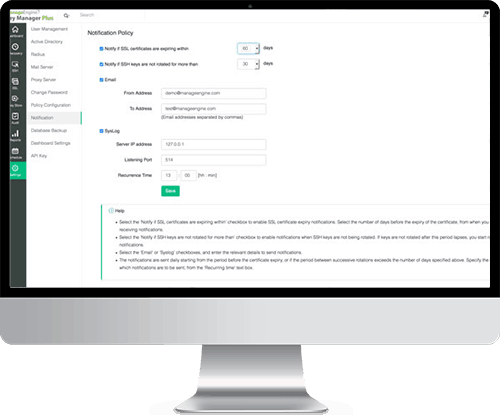
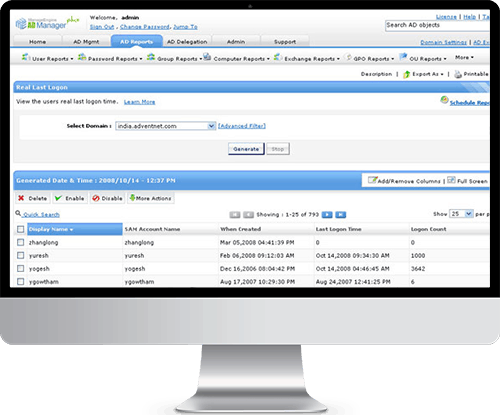
Your organizations’ IT infrastructure generates a huge amount of log data every day. These machine generated logs contain vital information that provide insights and network security intelligence into user behaviors, network anomalies, system downtime, policy violations, internal threats, regulatory compliance, etc. However, the task of manually analyzing these event logs and syslogs without an automated log analyzer tool can be time-consuming and painful.