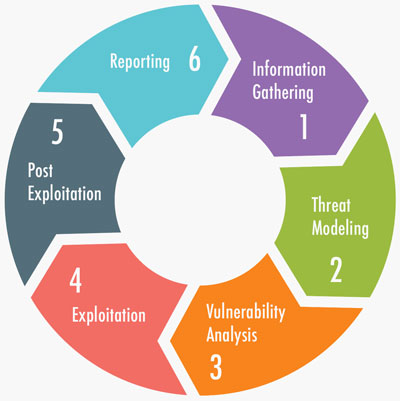
What is our methodology?
Our penetration testing methodology involves an attack simulation carried out by our highly qualified security consultants in an attempt to:
- identify security vulnerabilities present in the system
- Understand the level of risk for your organization
- Help resolve and correct identified network security vulnerabilities
High-Tech Network Security penetration testers have experience supporting network, devices, and hosts — not only trying to hack them. They use this expertise on sensitive issues to focus in, and provide actionable advice on remediation.