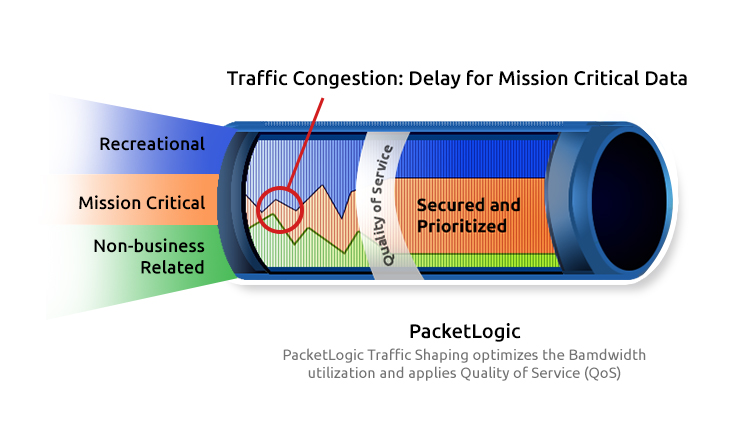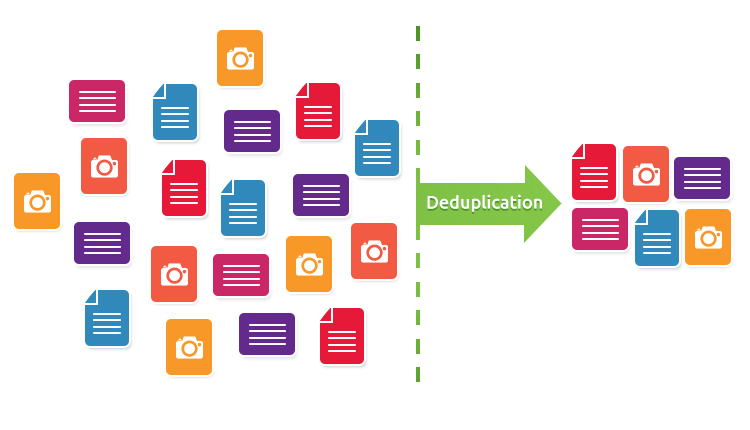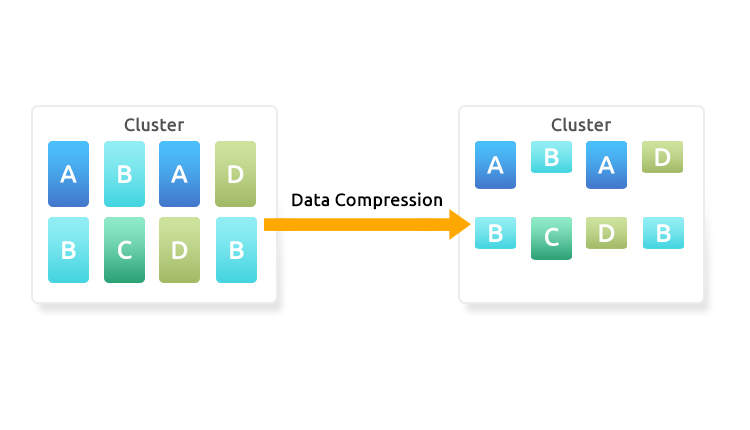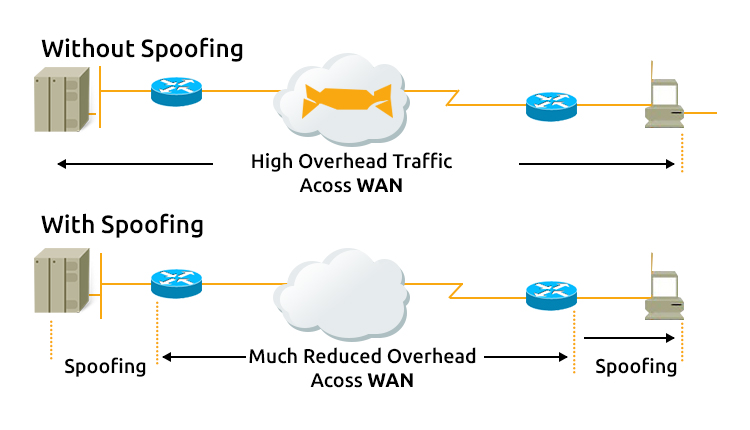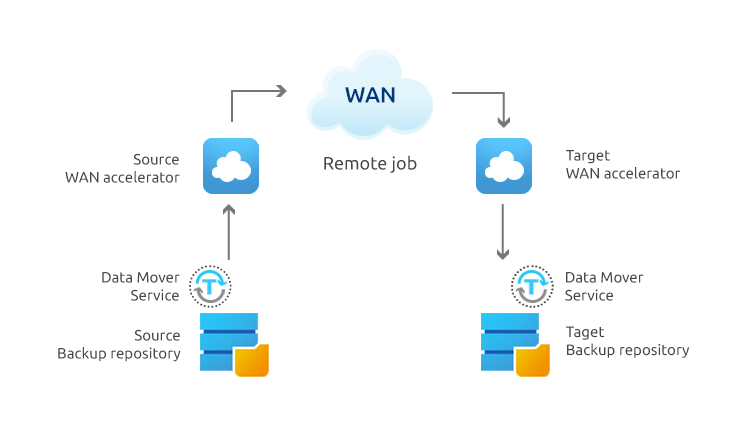
What is a WAN accelerator?
A WAN accelerator reduces the amount of data required to flow back and forth across the WAN with the use of caching and data compression. A WAN accelerator essentially works by storing duplicate files (or parts of files) so that they can be indexed in global cache instead of being sent across the WAN again. WAN accelerators effectively trade off network I/O for disk I/O, thus significantly improving the performance of data transfers over the network is therefore significantly enhanced in circumstances where bandwidth is the primary bottleneck.